Cybersecurity Alert: Malware Campaign Hijacks AI Video Generation Trend
As AI-video generation tools gain popularity, a wave of malicious activities is emerging, targeting unsuspecting users. A recent report from Mandiant and Google Cloud has unveiled a cyber campaign orchestrated by a group known as "UNC6032." This group has been actively flooding the online space with fake advertisements and phishing schemes aimed at exploiting the burgeoning interest in AI-driven tools.
The Rise of UNC6032
Since mid-2024, UNC6032 has proliferated thousands of advertisements across social media platforms, promising access to popular AI video creation tools such as Luma AI, Canva Dream Lab, and Kling AI. Each advertisement acts like bait, leading victims to counterfeit websites designed to harvest personal information.
![Alert: Mandiant Warns of Malware in AI Video Generators 2 Fake ads for AI-video generators that lead to phishing lures and deploy malware on victim devices. [Source: Mandiant and Google Cloud]](https://ainewsera.com/wp-content/uploads/2025/06/AD_4nXdgiFHRB8u39-eZYDudbK4TUR3OYWYjTW57LYJvUf6srY2zlXflVrzavfrHdhOiaHVP_7brv6Rkuy8rwA408ngkx3K-50Sv.png)
Phishing Tactics Exposed
Upon visiting these counterfeit platforms, victims find themselves on phishing pages that deploy malware to steal sensitive data. This includes login credentials, credit card information, and even Facebook account details. The campaign’s impact is widespread, with various industries and regions falling prey to these tactics.
Extensive Reach of UNC6032
Research from the Mandiant team indicates that thousands of ads associated with UNC6032 have reached millions of users through popular social media networks, notably Facebook and LinkedIn. According to Diana Ion, Rommel Joven, and Yash Gupta, the group’s tactics are constantly evolving to evade detection, making it more challenging for users to identify scams.
<script async src="https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-9958505722835444" crossorigin="anonymous"> <ins class="adsbygoogle" style="display:block; text-align:center;" data-ad-layout="in-article" data-ad-format="fluid" data-ad-client="ca-pub-9958505722835444" data-ad-slot="6218723755">
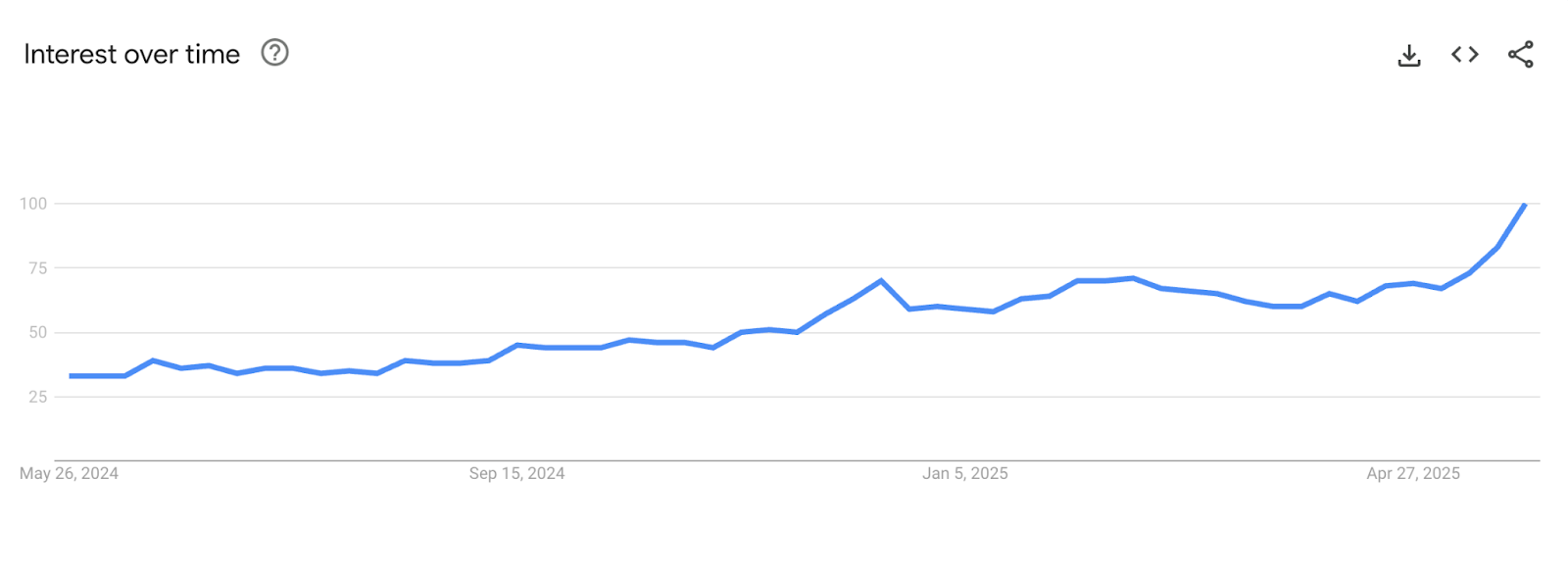
Surge in Interest: The Appeal of AI Video Generators
Since early 2024, the interest in AI video generation technology has surged dramatically. Google Trends data shows a notable spike in searches related to AI video tools, reflecting a growing fascination and curiosity among the public. The technology available today allows users to create lifelike scenes and characters with ease, elevating the risk of deception far beyond previous AI capabilities.
![Alert: Mandiant Warns of Malware in AI Video Generators 3 Graph from Google Trends showing the rise in internet searches for “AI video generator” over the past year. [Source: Google Trends]](https://ainewsera.com/wp-content/uploads/2025/06/AD_4nXdkQJNrgUlxSwrFHKP0jDTWKcx4dc-OkjS6Nyovtc21wTh2qOh6eSdrk24H-I7Di2eNkNG1XT2ymZ2s5a-OFQfPkPwBSMUP.png)
The Accessibility of AI Tools
Another factor contributing to the rise of this malware campaign is the lower barrier to entry for using AI technology. Cybersecurity firm Morphisec highlighted that, with advancements in AI tools, even individuals with minimal technical know-how can create convincing fake media. This accessibility has opened new doors for cybercriminals to exploit unsuspecting users and organizations.
<script async src="https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-9958505722835444" crossorigin="anonymous"> <ins class="adsbygoogle" style="display:block" data-ad-format="autorelaxed" data-ad-client="ca-pub-9958505722835444" data-ad-slot="6793438825">
Exploiting Trust: A New Scheme
Morphisec’s research sheds light on the unique nature of this campaign, which leverages AI as a social engineering tool. By turning a legitimate trend into an infection vector, hackers are targeting a more trusting and less cautious audience, including creators and small businesses exploring AI for productivity purposes.
Collaboration with Meta
Mandiant has acknowledged the proactive response of Meta, which was already monitoring and investigating the UNC6032 campaign prior to being notified. By utilizing Meta’s ad library, Mandiant identified over 30 counterfeit websites linked to thousands of fake ads predominantly circulated on Facebook.
Static Payloads Unleashed
Once users engage with these fake websites and submit prompts for video generation, the sites deploy malicious payloads hidden within their infrastructure. This intricate setup allows hackers to collect valuable data while compromising user devices.
<script async src="https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-9958505722835444" crossorigin="anonymous"> <ins class="adsbygoogle" style="display:block; text-align:center;" data-ad-layout="in-article" data-ad-format="fluid" data-ad-client="ca-pub-9958505722835444" data-ad-slot="6218723755">
Where is UNC6032 Based?
According to findings from Google Cloud, the UNC6032 group has a connection to Vietnam. Mandiant and Google Cloud refer to the term “UNC” to describe unique clusters of hacking activities that lack sufficient telemetry and information.
Potential Nexus to Vietnam
This connection does not imply a direct state-sponsored threat; instead, it suggests that UNC6032 may either be an offshoot of an existing group or a completely new entity using distinct methods and practices. While their activities are traced to Vietnam, attributing state-level involvement remains speculative.
The Bigger Picture: Industry Impact
As these phishing campaigns continue to spread, businesses and individuals must remain vigilant. The ability to effectively create and manipulate AI-generated content poses significant risks across many sectors, amplifying the impact of malicious activities by groups like UNC6032.
Cybersecurity Recommendations
Experts advise users to exercise caution while engaging with new platforms, especially those promoting AI technologies. Always verify the legitimacy of the sources and engage only with trusted providers to mitigate potential risks.
A Challenging Environment
The rapid evolution of cyber threats calls for
an equally rapid response from cybersecurity teams and individuals alike. As tech-savvy cybercriminals leverage emerging trends, the common user must adapt to safeguard personal and organizational data.
Conclusion: A Call to Action
While AI video generation tools present exciting possibilities, they also present a fertile ground for malicious actors like UNC6032. Awareness and proactive cybersecurity measures are essential in navigating this new landscape. As users, we must remain vigilant and continuously educate ourselves about potential threats to avoid falling victim to increasingly sophisticated scams.
Written by Derek B. Johnson, a seasoned cybersecurity reporter, who emphasizes the need for strong online defenses in a rapidly changing tech environment.
source